Change master specified by syncrepl of slave¶
The story of this entry is a supplement of previous migration(Migration OpenLDAP 2.3 to 2.4). The third step and fourth step is the same with first step, so I omit it. Current slave servers are OpenLDAP 2.3 on CentOS 5.4. We build New slave servers with OpenLDAP 2.4 on Ubuntu 12.04, but we must also operate legacy servers, because we don’t stop these at the this time. Need to remove database, when It is changed master server on slave.
The procedure on CentOS5.4 as slave server is follow.
$ sudo /sbin/service ldap stop
$ cd /var/lib
$ sudo tar zcvf /path/to/ldap_backup.tgz ./ldap
$ sudo -s
# rm ldap/{*log*,*db*,alock}
# exit
$ sudo /sbin/service ldap start
A legacy slave server is enable to replicate from a new master server as OpenLDAP 2.4 on Ubuntu 12.04.
Change slave to master of OpenLDAP 2.4 configuration¶
The story of this entry is previous migration second step (Migration OpenLDAP 2.3 to 2.4). Firstly set up as slave, then change config. Namely see “Replication from OpenLDAP 2.3 to 2.4”.
Disable replication¶
Delete “olcSyncrepl”, “olcUpdateRef” lines from “olcDatabase={1}hdb”.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase=hdb
Before
(snip)
olcAccess: {12}to * by * none
olcSyncrepl: {0}rid=xxx provider=ldaps://xxx.xxx.xxx.xxx bindmethod=simple binddn="cn=ldapadmin,dc=example,dc=org" credentials=xxxxxxxx searchbase="dc=example,dc=org" type=refreshAndPersist retry="5 10 60 +"
olcUpdateRef: ldaps://xxx.xxx.xxx.xxx
Changed
(snip)
olcAccess: {12}to * by * none
Load module¶
Load module syncprov for master.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config cn=module{0}
Before
0 cn=module{0},cn=config
objectClass: olcModuleList
cn: module{0}
olcModulePath: /usr/lib/ldap
olcModuleLoad: {0}back_hdb
Changed
0 cn=module{0},cn=config
objectClass: olcModuleList
cn: module{0}
olcModulePath: /usr/lib/ldap
olcModuleLoad: {0}back_hdb
add cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulePath: /usr/lib/ldap
olcModuleLoad: syncprov.la
Index¶
Delete “description eq” line from “olcDbIndex,olcDatabase={1}hdb”.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase=hdb olcDbIndex
Before
olcDbIndex: objectClass eq,pres
olcDbIndex: uid eq,pres,sub
olcDbIndex: uniqueMember,memberUid eq
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: cn eq
olcDbIndex: sudoUser eq,sub
olcDbIndex: description eq
olcDbIndex: entryCSN,entryUUID eq
Changed
olcDbIndex: objectClass eq,pres
olcDbIndex: uid eq,pres,sub
olcDbIndex: uniqueMember,memberUid eq
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: cn eq
olcDbIndex: sudoUser eq,sub
olcDbIndex: entryCSN,entryUUID eq
Access control¶
Insert a new writing “sshPublicKey” lines.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase={1}hdb olcAccess
Before
0 olcDatabase={1}hdb,cn=config
olcAccess: {0}to * by dn="cn=ldapadmin,dc=example,dc=org" write by * none break
olcAccess: {1}to attrs=userPassword by self read by anonymous auth by * none
olcAccess: {2}to dn.subtree="ou=ACL,ou=policy,dc=example,dc=org" by * compare by * none
olcAccess: {3}to dn.subtree="ou=Password,ou=policy,dc=example,dc=org" by * none
olcAccess: {4}to dn.subtree="ou=SUDOers,ou=policy,dc=example,dc=org" by * read by * none
olcAccess: {5}to dn.subtree="ou=People,dc=example,dc=org" by self read by * read
olcAccess: {6}to dn.subtree="ou=Group,dc=example,dc=org" by * read
olcAccess: {7}to dn.subtree="dc=example,dc=org" by * search by * none
olcAccess: {8}to * by * none
Changed
0 olcDatabase={1}hdb,cn=config
olcAccess: {0}to * by dn="cn=ladpadmin,dc=example,dc=org" write by * none break
olcAccess: {1}to attrs=sshPublicKey by self write by * none
olcAccess: {2}to attrs=userPassword by self read by anonymous auth by * none
olcAccess: {3}to dn.subtree="ou=ACL,ou=policy,dc=example,dc=org" by * compare by * none
olcAccess: {4}to dn.subtree="ou=Password,ou=policy,dc=example,dc=org" by * none
olcAccess: {5}to dn.subtree="ou=SUDOers,ou=policy,dc=example,dc=org" by * read by * none
olcAccess: {6}to dn.subtree="ou=People,dc=example,dc=org" by self read by * read
olcAccess: {7}to dn.subtree="ou=Group,dc=example,dc=org" by * read
olcAccess: {8}to dn.subtree="dc=example,dc=org" by * search by * none
olcAccess: {9}to * by * none
sizelimit¶
Add olcSizeLimit to “cn=config”.
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config cn=config
Before
0 cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/slapd/slapd.args
olcLogLevel: 128
olcPidFile: /var/run/slapd/slapd.pid
olcTLSCertificateFile: /etc/ssl/certs/hoge.pen
olcTLSCertificateKeyFile: /etc/ssl/private/hoge.key
olcToolThreads: 1
Changed
0 cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/slapd/slapd.args
olcLogLevel: 128
olcPidFile: /var/run/slapd/slapd.pid
olcTLSCertificateFile: /etc/ssl/certs/hoge.pen
olcTLSCertificateKeyFile: /etc/ssl/private/hoge.key
olcToolThreads: 1
olcSizeLimit: unlimited
syncprov overlay¶
Add a syncprov overlay DN.
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase={1}hdb
Before
0 olcDatabase={1}hdb,cn=config
(snip)
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: uniqueMember,memberUid eq
Changed
0 olcDatabase={1}hdb,cn=config
(snip)
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: uniqueMember,memberUid eq
add olcOverlay=syncprov,olcDatabase={1}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
setting LDAP client of master-self¶
Needs these setting in a master server.
/etc/ldap/ldap.conf
URI ldap://127.0.0.1
BASE dc=example,dc=org
TLS_CACERTDIR /etc/ssl/certs
TLS_REQCERT never
ssl start_tls
Postscript¶
Iou must not set up “/etc/ldap.conf” when using libpam-ldapd, libnss-ldapd. Especially, you will use OpenSSH-lpk, you must use libpam-ldapd and libnss-ldapd.
Confirmation¶
At least, this server as LDAP master of OpenLDAP2.4 on Ubuntu 12.04 is now available. Confirmation is using “ldapsearch” command and “id” command. And you also look on a audit.log of the slave server.
Replication from OpenLDAP 2.3 to 2.4¶
The story of this entry is previous migration first step (Migration OpenLDAP 2.3 to 2.4). Master and slave servers that are OpenLDAP 2.3 with slapd.conf on CentOS 5.4 are running currently. I have prepared OpenLDAP 2.4 with slapd-config on Ubuntu 12.04 as slave server.
Install packages¶
$ sudo apt-get install slapd ldap-utils
Debconf setting is follows;
slapd configuration¶
Administrator password
Confirm password
Setup OpenLDAP¶
I have set up with LDIF files of prepared schemas in previous story.
$ sudo vi /etc/default/slapd
default:
SLAPD_SERVICES="ldap:/// ldapi:///"
Changed:
SLAPD_SERVICES="ldap:/// ldaps:/// ldapi:///"
Restart slapd.
$ sudo service slapd restart
Change schemas¶
I have changed “core.schema” using ldapvi because the present core.schema had been customized.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config cn={0}core
(snip)
olcAttributeTypes: {51}( 1.2.840.113549.1.9.1 NAME ( 'email' 'emailAddress' 'pkcs9email' ) DESC 'RFC3280: legacy attribute for email addresses in DNs' EQUALITY caseIgnoreIA5Match SUBSTR caseIgnoreIA5SubstringsMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26{128} )
(snip)
The details of changes are omitted.
Import additional schema¶
I have added previous prepared schemas.
$ sudo ldapadd -Y EXTERNAL -H ldapi:// -f ~/local.ldif
$ sudo ldapadd -Y EXTERNAL -H ldapi:// -f ~/sudo.ldif
$ sudo ldapadd -Y EXTERNAL -H ldapi:// -f ~/openssh-lpk.ldif
$ sudo ldapadd -Y EXTERNAL -H ldapi:// -f /etc/ldap/schema/ppolicy.ldif
ppolicy is present by default, but not load.
Load module¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config cn=module{0}
Default is follow;
0 cn=module{0},cn=config
objectClass: olcModuleList
cn: module{0}
olcModulePath: /usr/lib/ldap
olcModuleLoad: {0}back_hdb
Change is follows;
0 cn=module{0},cn=config
objectClass: olcModuleList
cn: module{0}
olcModulePath: /usr/lib/ldap
olcModuleLoad: {0}back_hdb
add cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulePath: /usr/lib/ldap
olcModuleLoad: auditlog.la
add cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulePath: /usr/lib/ldap
olcModuleLoad: ppolicy.la
Use “add” command when using new dn.
Change suffix¶
Default suffix is “cn=admin,dc=nodomain”. I have replaced “admin” to “ldapadmin”, “dc=nodomain” to “dc=example,dc=org”. Changes lines are follow.
olcSuffix
olcAccess {0}, {2}
olcRootDN
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase=hdb
Default is follow;
0 olcDatabase={1}hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {1}hdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=nodomain
olcAccess: {0}to attrs=userPassword,shadowLastChange by self write by anonymous auth by dn="cn=admin,dc=nodomain" write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by self write by dn="cn=admin,dc=nodomain" write by * read
olcLastMod: TRUE
olcRootPW: {SSHA}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
olcDbCheckpoint: 512 30
olcDbConfig: {0}set_cachesize 0 2097152 0
olcDbConfig: {1}set_lk_max_objects 1500
olcDbConfig: {2}set_lk_max_locks 1500
olcDbConfig: {3}set_lk_max_lockers 1500
olcDbIndex: objectClass eq
olcRootDN: cn=admin,dc=nodomain
Change is follow;
0 olcDatabase={1}hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {1}hdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=example,dc=org
olcAccess: {0}to attrs=userPassword,shadowLastChange by self write by anonymous auth by dn="cn=ldapadmin,dc=example,dc=org" write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by self write by dn="cn=ldapadmin,dc=example,dc=org" write by * read
olcLastMod: TRUE
olcRootPW: {SSHA}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
olcDbCheckpoint: 512 30
olcDbConfig: {0}set_cachesize 0 2097152 0
olcDbConfig: {1}set_lk_max_objects 1500
olcDbConfig: {2}set_lk_max_locks 1500
olcDbConfig: {3}set_lk_max_lockers 1500
olcDbIndex: objectClass eq
olcRootDN: cn=ladpadimn,dc=example,dc=org
Index¶
objectClass and entryCSN,entryUUID is required for replication at least.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase=hdb olcDbIndex
Default:
olcDbIndex: objectClass eq
Changed:
olcDbIndex: objectClass eq,pres
(snip)
olcDbIndex: entryCSN,entryUUID eq
Other changes are ommitted.
TLS Certifiation¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config cn=config
Add path of certification and key file to olcTLSCertificateFile, olcTLSCertificateKeyFile.
for example, using /etc/ssl/private/hoge.key and /etc/ssl/cert/hoge.pem,
Default
0 cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/slapd/slapd.args
olcLogLevel: none
olcPidFile: /var/run/slapd/slapd.pid
olcToolThreads: 1
Changed
0 cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/slapd/slapd.args
olcLogLevel: none
olcPidFile: /var/run/slapd/slapd.pid
olcToolThreads: 1
olcTLSCertificateFile: /etc/ssl/certs/hoge.pem
olcTLSCertificateKeyFile: /etc/ssl/private/hoge.key
LogLevel¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config cn=config olcLogLevel
Default
0 cn=config
olcLogLevel: none
Changed
0 cn=config
olcLogLevel: 512
Change rsyslog setting when next error occurs.
rsyslogd-2177: imuxsock lost 228 messages from pid 2547 due to rate-limitin
Add follow parameter to /etc/rsyslog.conf
# Disable rate limiting
# (default is 200 messages in 5 seconds; below we make the 5 become 0)
$SystemLogRateLimitInterval 0
Restart rsyslog.
$ sudo service rsyslog restart
DB Cachesize¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase=hdb olcDbCacheSize
Default:
0 olcDatabase={1}hdb,cn=config
Changed:
0 olcDatabase={1}hdb,cn=config
olcDbCacheSize: 2000
DB IDL Cache size
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase=hdb olcDbIDLcacheSize
Changed:
0 olcDatabase={1}hdb,cn=config
olcDbIDLcacheSize: 2000
Access control¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase={1}hdb olcAccess
Default:
0 olcDatabase={1}hdb,cn=config
olcAccess: {0}to attrs=userPassword,shadowLastChange by self write by anonymous auth by dn="cn=ldapadmin,dc=example,dc=org" write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by self write by dn="cn=ldapadmin,dc=example,dc=org" write by * read
Changed:
0 olcDatabase={1}hdb,cn=config
olcAccess: {0}to * by dn="cn=ldapadmin,dc=example,dc=org" write by * none break
olcAccess: {1}to attrs=userPassword by self read by anonymous auth by * none
olcAccess: {2}to dn.subtree="ou=ACL,ou=policy,dc=example,dc=org" by * compare by * none
olcAccess: {3}to dn.subtree="ou=Password,ou=policy,dc=example,dc=org" by * none
olcAccess: {4}to dn.subtree="ou=SUDOers,ou=policy,dc=example,dc=org" by * read by * none
olcAccess: {5}to dn.subtree="ou=People,dc=example,dc=org" by self read by * read
olcAccess: {6}to dn.subtree="ou=Group,dc=example,dc=org" by * read
olcAccess: {7}to dn.subtree="dc=example,dc=org" by * search by * none
olcAccess: {8}to * by * none
OpenLDAP 2.4 needs the rule of ‘to dn.subtree=”dc=example,dc=org” by * search by * none’, OpenLDAP 2.3 does not needs.
auditlog¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase={1}hdb
Changed:
0 olcDatabase={1}hdb,cn=config
(snip)
add olcOverlay=auditlog,olcDatabase={1}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcAuditLogConfig
olcOverlay: auditlog
olcAuditlogFile: /var/log/ldap/audit.log
make directory.
$ sudo mkdir /var/log/ldap
$ sudo chown -R openldap: /var/log/ldap
ppolicy¶
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase={1}hdb
Changed:
0 olcDatabase={1}hdb,cn=config
(snip)
add olcOverlay=ppolicy,olcDatabase={1}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcPPolicyConfig
olcOverlay: ppolicy
olcPPolicyDefault: cn=default,ou=Password,ou=policy,dc=example,dc=org
olcPPolicyUseLockout: TRUE
Replication¶
olcDbIndex entryUUID must be “eq”. Change rid, provider, and credentials of follow.
$ sudo ldapvi -Y EXTERNAL -h ldapi:/// -b cn=config olcDatabase=hdb
Default:
(snip)
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: uniqueMember,memberUid eq
Changed:
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: uniqueMember,memberUid eq
olcSyncrepl: rid=xxx provider=ldaps://xxx.xxx.xxx.xxx bindmethod=simple binddn="cn=ldapadmin,dc=example,dc=org" credentials=xxxxxxxx searchbase="dc=example,dc=org" type=refreshAndPersist retry="5 10 60 +"
olcUpdateRef: ldaps://xxx.xxx.xxx.xxx
If you change master server, choise one of two method.
Remove current syncrepl setting and restart slapd, then add new syncrepl setting. (Don’t forget restart slapd.)
Stop slapd, then remove /var/lib/ldap/*, start slapd, change syncrepl setting.
Change parameters are rid, master server uri, and credential. You must execute plan 2) when there is next message on Syslog. This time setting only user for replication and the access control has been omitted.
Sep 13 19:27:08 ldaptest01 slapd[3272]: do_syncrepl: rid=xxx rc -2 retrying
Sep 13 19:28:08 ldaptest01 slapd[3272]: do_syncrep2: rid=xxx LDAP_RES_SEARCH_RESULT (53) Server is unwilling to perform
Sep 13 19:28:08 ldaptest01 slapd[3272]: do_syncrep2: rid=xxx (53) Server is unwilling to perform
ldap client for self¶
Install libnss-ldapd, libpam-ldapd but not libnss-ldap, libpam-ldap.
$ sudo apt-get install libnss-ldapd libpam-ldapd nslcd
/etc/nsswtich.conf and /etc/pam.d/common-{account,auth,password,sesson,session-noninteractive} are changed by Debconf of postinst.
nslcd configuration¶
LDAP server URI:
LDAP server search base:
dc=example,dc=org
Check server’s SSL certificate:
never
nslcd¶
/etc/nslcd.conf
uid nslcd
gid nslcd
uri ldap://localhost
base dc=example,dc=org
ssl start_tls
tls_reqcert never
/etc/ldap/ldap.conf
URI ldap://localhost
BASE dc=example,dc=org
TLS_CACERTDIR /etc/ssl/certs
TLS_REQCERT never
ssl start_tls
/etc/nslcd.conf
uid nslcd
gid nslcd
uri ldap://127.0.0.1
base dc=example,dc=org
pam_authz_search (&(objectClass=posixAccount)(uid=$username)(description=admin)
Postscript¶
Iou must not set up “/etc/ldap.conf” when using libpam-ldapd, libnss-ldapd. Especially, you will use OpenSSH-lpk, you must use libpam-ldapd and libnss-ldapd.
Confirmation¶
At least, replication of from the master of OpenLDAP 2.3 on CentOS5.4 to the slave OpenLDAP2.4 on Ubuntu 12.04 is now available. Replication is going to be running at the stage has been set for replication. Whether replication is done, you can be found at audit.log. Other confirmation is using ldapsearch command and id command.
Migration OpenLDAP 2.3 to 2.4¶
Current LDAP servers are CentOS 5.4 and OpenLDAP 2.3 with slapd.conf. I will replace these as Ubuntu 12.04 and OpenLDAP 2.4 with slapd-config. I write notes so I tested the migration.
System envrironment¶
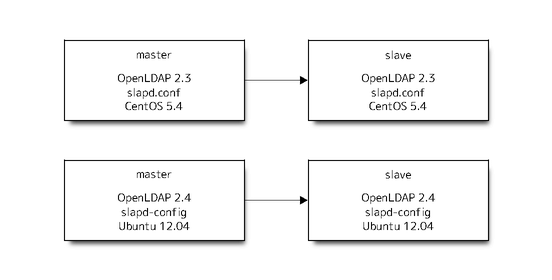
Current is like this.
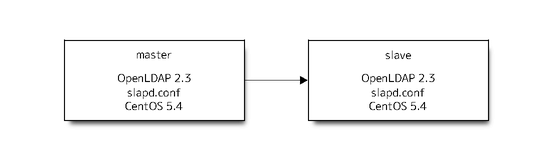
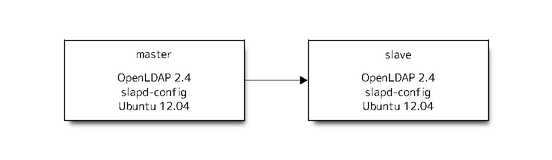
New will be next.
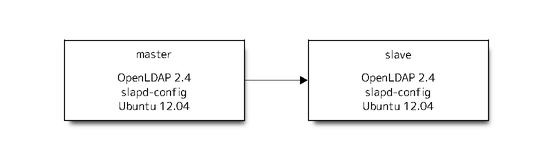
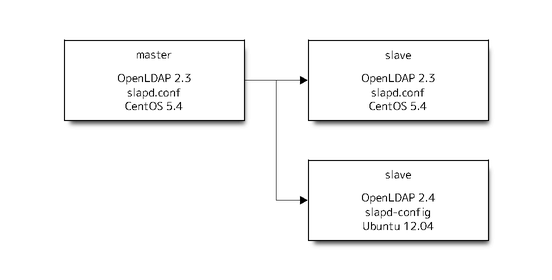
Step of migration is next.
Prepare a new master as slave of current
Change a new master as slave to master
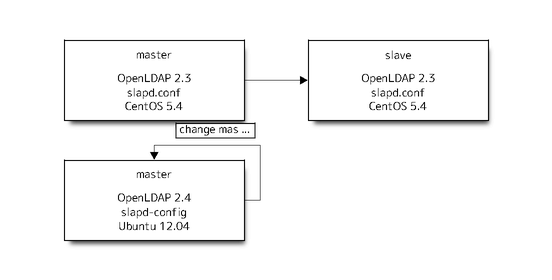
Prepare a new slave
Stop current LDAPs
sammary of setting up¶
I tried to convert with slaptest. slaptest is needed to convert custom schema to ldif. But this method has next failures.
Additional schemas are not included
Custom and additiona modules are not loaded
Database setting is not converted all
Access control is not converted
Global settings as LogLevel and TLS Certification etc are not converted
Overlay as like ppolicy and syncrepl etc are not converted
In other words, it means almost useless with slaptest, except of converting custom schema to LDIF. So I basically have set up using ldapvi.
Install packages¶
I had installed next packages.
slapd
ldap-utils
ldapvi
nslcd
Debconf asked these parameters when some packages installed. Second level items are set up values this time.
slapd¶
Administrator password
Confirm password
nslcd¶
LDAP server URI
LDAP server search base
dc=example,dc=org
Check server’s SSL vertificatte
never
Convert additional schema to LDIF¶
I converted additional schema to LDIF with slaptest after I installed slapd. I made temporary directory and copying files as slapd.conf, schema files as local.schema, sudo.schema, openssh-lpk.schema from current slave server of CentOS5.4.
$ sudo service slapd stop
$ cd /tmp
$ mkdir -p slapd.d/cn\=config/cn\=schema
$ cp -i slapd.conf .
$ cp -i local.schema sudo.schema openssh-lpk.schema slapd.d/cn\=config/cn\=schema/
$ sudo slaptest -f slapd.conf -F /tmp/slapd.d/
$ cd /tmp/slapd.d/cn\=config/cn\=schema
$ sudo mv -i cn\=\{4\}sudo.ldif sudo.ldif
$ sudo mv -i cn\=\{6\}local.ldif local.ldif
$ sudo mv -i cn\=\{7\}openssh-lpk.ldif openssh-lpk.ldif
Don’t forget to delete last 9 lines of each generated LDIF files.
I copied certification and private key files from current slave server. For example, it is as follows.
/etc/ca-certificates/myserver.key
/etc/ca-certificates/myserver.crt
Using ldapvi¶
ldapvi is “is an interactive LDAP client for Unix terminals. Using it, you can update LDAP entries with a text editor”. Debian package name is the same.
For example of changing it is as follows.
$ sudo ldapvi -Y EXTERNAL -h ldapi:// -b cn=config olcDatabase={1}hdb olcRootDN
----
0 olcDatabase={1}hdb,cn=config
olcRootDN: cn=admin,dc=nodomain # <- before
olcRootDN: cn=admin,dc=example,dc=org # <- after
----
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
1 entry read
add: 0, rename: 0, modify: 1, delete: 0
Action? [yYqQvVebB*rsf+?] y
Done.
Action of ldapvi are follows:
y commit changes
e open editor again
Y commit, ignoring errors
v view changes as LDIF change records
V view changes as ldapvi change records
+ rewrite file to include schema comments
b show login dialog and rebind
B toggle SASL
* set SASL mechanism
s skip one entry
f forget all deletions
q save changes as LDIF and quit
Q discard changes and quit
see also ldapvi User Manual .
Detail of Setting up as slave using ldapvi will be posted next time.
Fail testing pep8 with travis-ci¶
I use travis-ci for GitHub, but test_pep8 failed.
$ pip install -r requirements.txt --use-mirrors
Downloading/unpacking pep8 (from -r requirements.txt (line 1))
Downloading pep8-1.3.3.tar.gz
Running setup.py egg_info for package pep8
(snip)
Successfully installed pep8 minimock
Cleaning up...
$ nosetests
............E....
======================================================================
ERROR: tonicdnscli.tests.test_pep8.test_check_pep8
----------------------------------------------------------------------
Traceback (most recent call last):
File "/home/travis/virtualenv/python2.7/local/lib/python2.7/site-packages/nose/case.py", line 197, in runTest
self.test(*self.arg)
File "/home/travis/builds/mkouhei/tonicdnscli/src/tonicdnscli/tests/test_pep8.py", line 25, in test_check_pep8
runner = pep8.input_file
AttributeError: 'module' object has no attribute 'input_file'
----------------------------------------------------------------------
Ran 17 tests in 0.070s
FAILED (errors=1)
Done. Build script exited with: 1
Cause is version of pep8 module. Travis-ci’s is 1.3.3, but Debian GNU/Linux Sid as my environment is 1.2. So I have appended version of pep8 to requirements.txt.
pep8==1.2
minimock